Jenkins SECURITY-3314/SECURITY-3315 Mitigation
Over the last couple weeks, Ellucian noted that there is a critical security hole found in version of Jenkins that's currently required by ESM. The security hole involves the SSH plugin and the CLI HTTP endpoint as detailed below.
While they did provide the fix for this, the instructions were a bit confusing and did not provide any screenshots.
Thus, here are (hopefully) some clearer steps on how to disable the SSH plugin and CLI HTTP endpoint.
Step 1: Login into Jenkins and access Security
- Login to the ESM Jenkins instance as the admin user
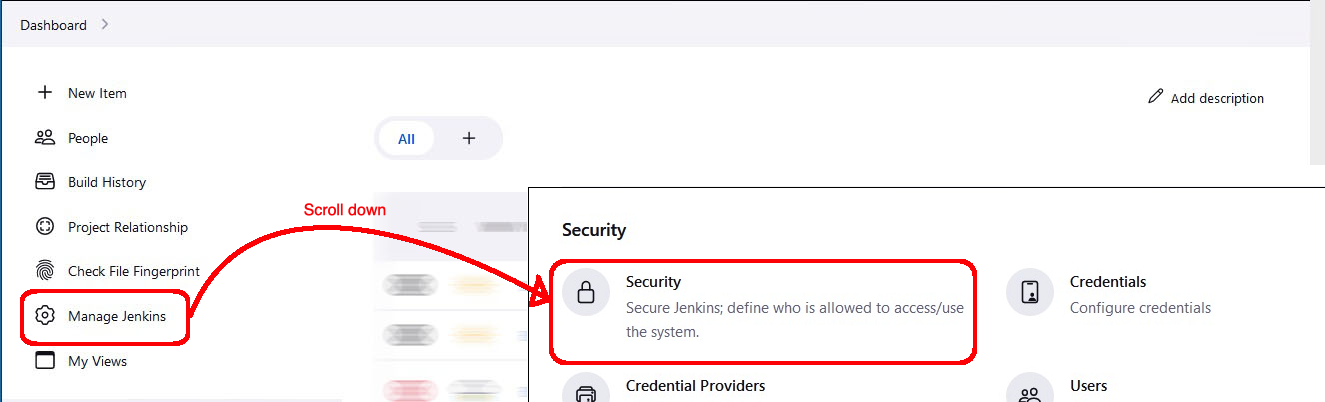
- Click Manage Jenkins
- Scroll down and then click Security
Step 2: Disable SSH
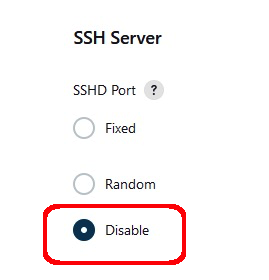
- Scroll down to SSH port and click Disable
Step 3: Disable CLI HTTP Endpoint
As the jenkins admin user:
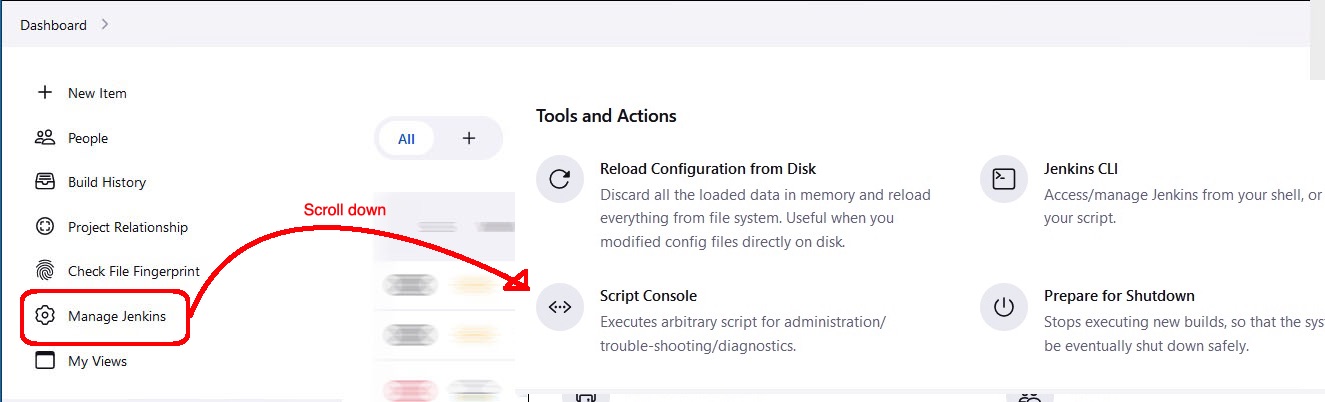
- Click Manage Jenkins
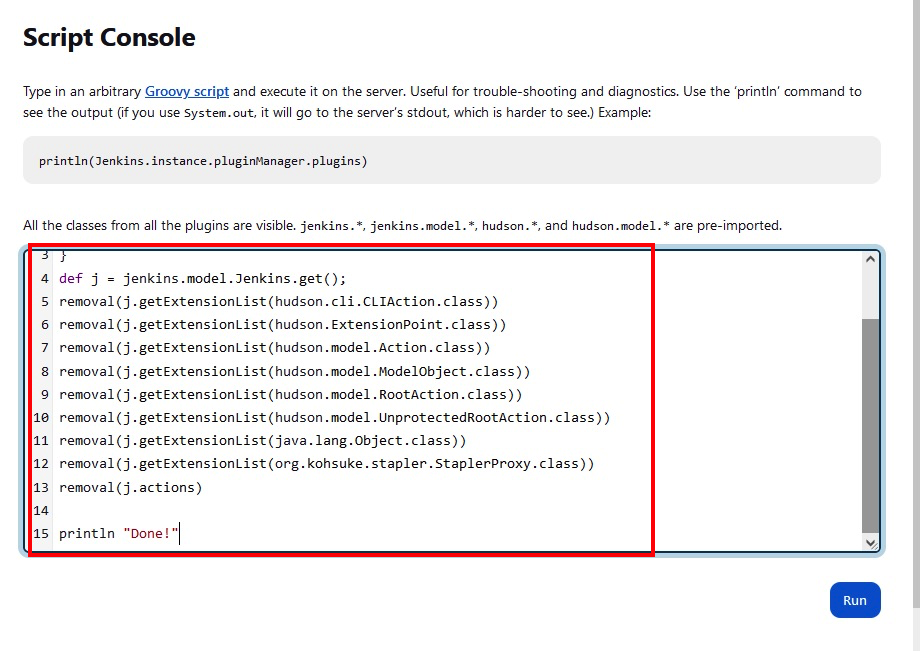
- Scroll down and then click Script Console
- To disable the CLI, paste contents of the disable-cli.groovy file into the script console.
- This will disable the CLI. However it will be re-enabled once jenkins is restarted.
- To permanently disable the CLI, do the following:
- SSH to the ESM server as the esmadmin user.
- cd /u01/jenkins (or where-ever jenkins is installed on your server)
- within the Jenkins directory, create a subdirectory called init.groovy.d --- all files within this directory are executed when jenkins starts up.
- copy the file disable-cli.groovy into the init.groovy,d subdirectory
- This file will now be executed each time jenkins starts up.